Unfortunately, phishing is a regular part of our lives these days and is especially bad in situations like the COVID-19 crisis. Everybody is on high alert already and bad news seem to come from all around us. Malicious actors have taken note and phishing scams have skyrocketed. While some phishing attempts are easy to spot, others can look almost legitimate. Here some basic methods are discussed that show how you can become more vigilant in order to protect yourself from phishing. Make no mistake, this topic really concerns everybody, and everybody is likely to fall for an attempt sooner or later.
Introduction
Articles like this one are just some scary news that we are faced with these days. Furthermore, most of us are in unusual situations and settings at the moment. This is an ideal playground for malicious actors that try to trick people by e-mail, text, or phone. In order to stay secure you should follow some basic rules on how to prevent phishing and vishing.
Phishing attempts generally play into basic human emotions: Be it fear, anger, greed, pride … If a phishing e-mail gets you emotional, it’s more likely that you will fall for the scam.
Note: This article is intended for the standard person out there. If you are a high-value target, you should probably consider further measures in addition to the ones described here. As always: What you have to do to keep safe depends on your target profile and your potential adversaries, however, this article might still have some interesting information for you.
The gist
Always remember you are the weakest link in the chain and can get phished / vished. Be vigilant!
Phishing
Be it by text or by e-mail, you can be safer by following these recommendations:
- Make sure you have up-to-date anti-virus software installed on your computer.
- Ask yourself for every message you receive if the sender is legitimate and if the text reads correct. Does this sender usually write in this style? Do you expect them to send you a link / an attachment?
- Check a link by hovering over it with your mouse and make sure it actually displays a legitimate address.
- Check that websites display a valid certificate in the browser and that the website uses
https - Instead of clicking on a link in an e-mail from your bank, navigate to the banks website according to your bookmark. This way, even if an e-mail is a phish, it will have no consequences because you don’t click on it.
- When in doubt delete a message without opening it and / or ask the sender directly if the message was legitimate.
Vishing
Voice phishing has become a common occurrence as well. Some basic recommendations to stay safe:
- Don’t answer phone numbers you don’t recognize.
- If in doubt on who is calling, if something feels off, you can call the caller back at a number that you know or get from a legitimate source, i.e., your banks website.
- Never disclose personal information to callers!
- A caller under distress / a good social engineer can make you feel very emotional about a situation. Keep your cool: things are hardly ever as serious as we think they are.
Phishing
Phishing generally takes place via e-mail, however, has already become fairly frequent via text messenger (Signal, Wire, Wickr, … whatever you use!). Be it the prince of Nigeria or “your bank” that has detected irregularities in your account and you need to react right away: these attempts often start with a simple e-mail. Sometimes these e-mails even come from your friends. I seem to have some acquaintances that fairly regularly get their e-mail accounts or contact lists hacked or stolen and I receive e-mails “from them” with links on stuff to check out.
These cases are fairly easy to spot some cases are more difficult. A true story: The company I work for does regular “phishing tests” where they try to phish their employees to teach them to be vigilant. Most of these attempts are blatantly obvious. However, even one of those poor attempt got me once. In order to understand the situation you need to know that employees at this company in general travel fairly frequently nationally and internationally. During the Ebola crisis in Africa I received an e-mail saying that some of my co-workers have gotten infected and that attached is a list of these people and what to look out for. The e-mail was written more eloquently, but as you can see already, basic privacy considerations already make this e-mail suspicious at least. In this situation I was in fact busy with some other task, briefly came into my office to grab something, and quickly checked my e-mails. I saw this e-mail and opened the attachment with a nice note from the people in cyber security letting me know that I shouldn’t have done this.
Let’s analyze the situation: When I opened the e-mail I was stressed. I actually had no time to read e-mails and should have left my office with whatever I came to grab. However, the news were constantly going on about new Ebola outbreaks, people getting screened at airports, etc., so this topic was front and center in many minds; very similar to the current COVID-19 crisis. Finally, I was also very curious who got it, I’m not going to talk myself out of this. In summary multiple emotions were present and triggered: stress, fear, and curiosity.
To prevent phishing, read through the following checklist on what to do and what not to do. Finally, some tips will be discussed to secure your e-mail client and some further reading and listening is provided.
E-Mail checklist
This is the most basic checklist that you should always go through before clicking on a link or opening an attachment. The checklist is fairly short and shouldn’t take you a lot of time but it will help you to stay safe. Important: Before relying on these tips and tricks test them out and make sure you understand them!
Are you expecting this?
First ask yourself if you are expecting this e-mail from this specific sender. If yes, chances are it’s not a phishing e-mail. Also think if the sender has sent you e-mails like this before: do these e-mails typically include links? Do you typically get attachments from this sender? At this stage look for anything that is out of the ordinary.
If the sender is a company such as your bank, your broker, etc., make sure it looks right. Many banks have security features in their e-mails. You should familiarize yourself with what these features are. Anybody can download the logos of your bank and create an authentic looking e-mail. Furthermore, a bank will never ask you to click on a link to log into your account (more about this further down).
If you are not expecting this e-mail, don’t click on links or open attachments. Ask the person if the in fact sent you something if you think its important, otherwise just delete the e-mail. Do not get curious!
Check URLs
Even if you are expecting a specific link, you should still check its URL. In many e-mail clients you can hover over a link without clicking it and the e-mail client / program will show you where the link points to. An example when using Thunderbird can be seen here:
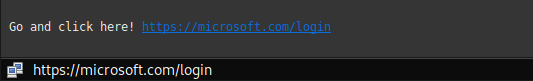
You can see that Thunderbird displays the actual link address that you would go to when clicking on this link. It agrees with the link address that is displayed in the e-mail message (by the way, I have no idea if this link actually leads anywhere).
A malicious link can look exactly identical, however point to some other website than the one it displays. This is shown in the following example:
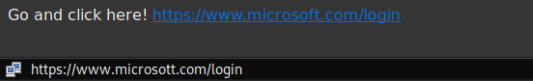
Another way that URLs can seem to be okay but are in fact not is when you look at very long links. Below screenshot, taken from Wikipedia shows what looks like the PayPal website, however, the URL in fact points somewhere different.

The URL starts with paypal.com, so, at first glance, it looks legitimate, however, don’t be fooled. The .com is not the the domain of the address, but must be related to a subfolder. The domain itself must be followed by a ‘/’ before going into further site structure. Here the domain continues with -us.cgi..., so it is not a legitimate URL that belongs to PayPal but tries to look that way. Suspicious.
Some e-mail providers, such as protonmail ask you to confirm if you want to really open a link after clicking on it. This will look like below:
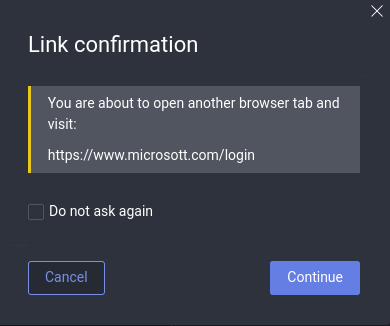
This little pop up is very helpful because it displays the correct URL that you will navigate to if you click okay below. This gives you another chance to double check the URL. While it seems annoying in certain situations, you can use these tools to train yourself to check URLs. Looking at the example you can see that it is the same link as the one we declared to be bad before.
Check URLs on mobile
Many of us check their e-mails on their phones or other mobile devices, so link checking can be more difficult. If you use the protonmail e-mail client on mobile you get the same link checking as with their web page. This will look like the example below:
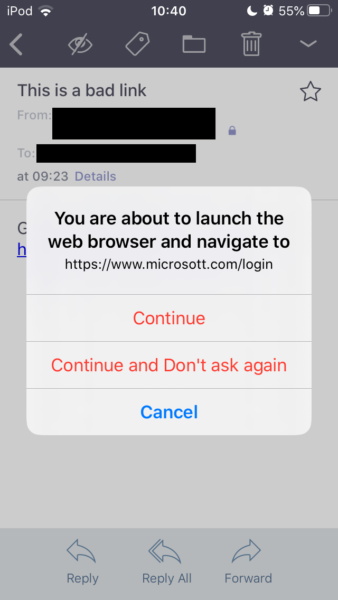
However, even if you don’t use protonmail, you can still double check links in e-mails, but you have to be more careful. Important: Before following this procedure on a potential phishing e-mail, test it out on your mobile device such that you make sure you understand how it works! On iOS for example you can long click any given link. However, some iOS apps will automatically load a preview if you try this. This preview is basically identical to loading the website, thus you cannot copy a link if this happens or you need to turn previews off. Without previews, a long click will give you a popup menu as below:
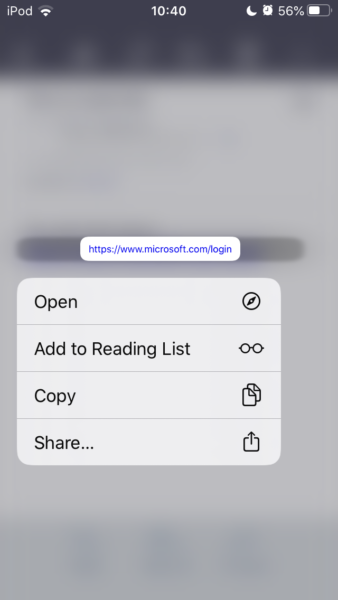
You can now copy the link to the clipboard without opening it. Again, test this out, because if you do not click long enough and you don’t have any protection, you will basically have clicked on the link now.
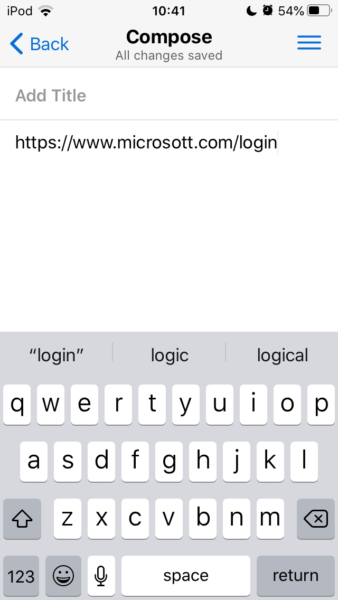
Then, open a note taking app (I recommend Standardnotes) and paste the URL into a new note. Now you can actually see the real URL as shown below and not just the text the sender chose to display for the URL. Again, you can see that this is our malicious URL example from before.
Attachments
Attachments can contain malicious code as well, so think twice before opening any attachment. The sender, e-mail body context, and attachment name can give some idea on if the attachment is legit or not. Are you expecting an attachment? Does the e-mail itself discuss the attachment? Do you believe that the sender actually wrote the e-mail and attached the document?
One good way of securing your computer is to have a reputable anti-virus software installed. Make sure your anti-virus software is up to date and scans incoming e-mails automatically.
If in doubt, do not open the attachment and ask the sender directly if it is an intended filed and / or delete the e-mail.
Logins
Many phishing attacks consist of trying to steal your credentials by sending you to a website that looks often identical to the website that it claims to be, but is in fact a malicious site. If you have already clicked on a link (maybe without checking, maybe it’s a superb phishing attempt) and you are prompted to enter your credentials for a website, e.g., your bank take a step back and check if everything is correct.
- Check if the URL that is displayed is actually the correct URL, or is it a URL that is suspicious? See the Paypal example above for some idea on how a spoofed URL can look.
- Check the certificate on a website: A legitimate website should always encrypt the transported traffic. Such websites start with
httpsinstead ofhttp, the additionalsstanding for secure. A certificate authority, an organization our browser trusts, signed a certificate for this website ensuring it belongs to who it says it belongs to. In Firefox for example, a gray padlock displayed on the right side of a URL. Clicking on this padlock gives us information if the website is secure or not, i.e., if the certificate is signed by a certificate authority.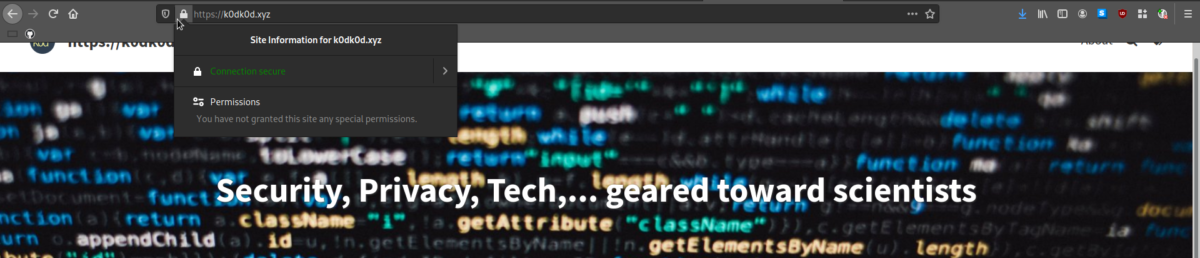 You can also display information on who signed the certificate and for which website it is valid. More information on how to do these checks can be found here. A good way to make sure you use
You can also display information on who signed the certificate and for which website it is valid. More information on how to do these checks can be found here. A good way to make sure you use httpsin any possible scenario is to install the HTTPS Everywhere browser plugin from the electronic frontier foundation (EFF).
The best way to ensure that you are actually dealing with, e.g., your bank is by not relying on the link in a given e-mail at all. You have probably saved the URL to your banks online login site or you remember it. Never click on a link in the e-mail and use your credentials to log in. You should instead always just open a browser, navigate to your bookmark of your, e.g., bank’s login page, and enter your credentials there. If the e-mail was a phish nothing has happened and you probably won’t find in your account whatever the e-mail claimed. This way however you ensured that you really only used your credential on the website of your bank.
Secure your e-mail client
Another way of potentially being able to introduce malicious code into your system is by having the e-mail client of the recipient automatically load images, etc. To avoid this, e-mail clients should come configured in a way that prevent such content from automatically being displayed. In Thunderbird for example this additional layer of protection looks like this:

Similar features are available for web clients, e.g., protonmail, and look like this:
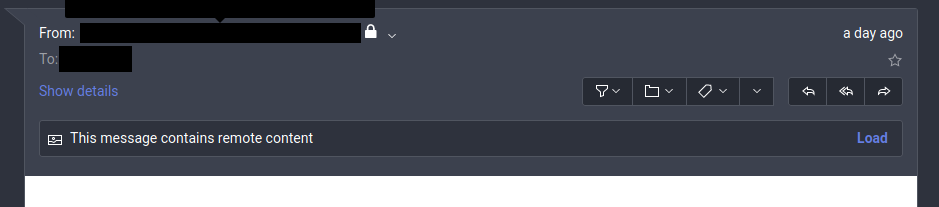
In order to load the remote content you have to actively click on the load button. Again, before doing so consider what is discussed above and ask yourself if it is necessary.
Summary
In summary, we discussed a few basic rules on how to deal with potential phishing attacks. In such an attack, you are the weakest link in the chain. This is not something to be ashamed of but is simply part of what makes us human. Always ask yourself if an e-mail is legitimate or not, and if you are not sure of the legitimacy, ask the person who sent it before opening it by, e.g., calling.
I have received many texts and e-mails from friend that sometimes only contain a link. And sure, for some of my dear friends this is normal behavior. However, if I’m in doubt if a URL is legitimate, I will ask back and check in with the sender if a specific message was sent on purpose. Don’t click on a link that you can’t verify!
Further information
There are many further sources out there as well as case studies. This post is only meant as an overview to what you can and should do, i.e., to present the basics. To continue reading and inform yourself on phishing and potential attacks have a look at the following resources and don’t hesitate to search for more information online:
- Protonmail blog with many other valuable information on phishing, use the search function for more.
- Symantec article on phishing and how to prevent it.
If you want to go down the rabbit hole further and listen to one possible worse case scenario that start with a fairly targeted and elaborate phish I recommend listening to episode 3 of Darknet diaries: DigiNotar, You are the Weakest Link, Good Bye!.
Vishing
Unfortunately, voice phishing, commonly referred to as vishing, has become more common. This can, e.g., be the tax authority or your bank calling you. It is generally good practice to not answer unknown phone numbers. You should also beware of known phone numbers. Spoofing of numbers, i.e., making it look like you call from a specific number, is extremely easy these days and regularly used by malicious actors.
One of your services calls you
If your bank or some other service that you regularly interact with calls you, alarm bells should go off in your brain. This is probably not a normal scenario. You do no harm by taking down the information of the caller, however, under no circumstances give out personal information, credit card numbers, account numbers, etc. If you believe that the call is legitimate, tell the person that you will call them back at the phone number that your bank publishes online. This way you can make sure who is on the other end of the line.
Somebody in an emergency calls you
Phone calls trying to social engineer a person to disclose information have been commonly heard of as well, especially the ones that target senior citizens and try to rob money from them by trying to get their credit card information. Again, you can always call the person that needs something back. Never give out your personal information in a call that you receive.
Emotions
Many of these vishing calls play, like phishing attempts, on your emotions, e.g., something bad happened to your bank account or somebody is in a hospital and needs money now. These are high-stress situations that we are put into, however, none of the situations if we really think about them require immediate action. Always remember, you could have missed a call easily. If you have doubts about caller, call the person you think is on the line back. Otherwise, hang up and ignore it.
As mentioned in an earlier post on podcasts there is an excellent, fictional, podcast out there on vishing, called Motherhacker. If you have some time and want to listen to an excellently produced story, you’re welcome. If you want to think about the story from a security point of view, think about what you could do to prevent something like this from happening to you. And if you just want to enjoy the show: That is completely fine as well.
Stay vigilant!
-k0dk0d
2020-04-28 Update: This article previously did not mention that iOS long clicks on link might produce a preview, which is the same as loading a link. The current version corrects this. Furthermore: the mediaplayer to the darknet diary episode was removed due to trackers.
